By Patrick Colbeck
Big Media, Big Tech, and Big Government would all have us believe that the 2020 election was “the most secure election in American history.”
Was it?
In order to answer this question effectively, we need to examine the integrity of our election systems. In particular, we need to examine the electronic voting systems which manage the execution of our key election processes such as the all-important tabulation of the vote. I have compiled evidence of electronic voting system vulnerabilities for your consideration that you may not have heard about…at least not heard about since November 3, 2020.
Pre-November 3, 2020
Before November 3, 2020, there was bi-partisan concern with the integrity of our election systems.
As a Republican State Senator, I requested an investigation into irregularities that were apparent in Detroit’s election system, despite the fact that the 2017 election had already been certified in favor of the Republican presidential candidate, Donald Trump.
As it turns out, I wasn’t the only one concerned with election integrity prior to November 3, 2020. Months before the election the Cybersecurity Infrastructure Security Agency (CISA) released the following “Critical Infrastructure Security and Resilience Note”. The note provided an extensive review of election system vulnerabilities and the impacts of any exploits of these vulnerabilities.
The release of the CISA report was followed by the release of the following report by the Michigan Election Security Commission just a month prior to the 2020 election.
Much as with the CISA note, the MESC report provided a list of significant risks to the integrity of our election system.
What evidence do we have that any of the security risks identified in these reports were mitigated or eliminated in any meaningful way before the November 3, 2020 election? None.
These reports were not the only indicators of risks to our electronic voting systems prior to the election. Investigator Kanekoa the Great has compiled an extensive list of others who expressed concerns with the integrity of electronic voting systems in particular.
As a point of fact, it was quite in vogue for Democrats in particular to highlight the vulnerabilities of electronic voting systems in the wake of the 2016 presidential election. It fit nicely with their demonstrably false “Russian Collusion” narrative that included the dismissal of Hunter Biden’s laptop as “Russian disinformation”. Their commitment to this narrative was significant enough for them to have challenged the results of the 2016 election.
Going on three years of election fraud investigations, I have seen ZERO evidence that any of the election integrity concerns cited by numerous public officials before November 3, 2020 were ever addressed prior to the election. Despite this fact, these same individuals and their accomplices in the media now label anyone making these same assertions regarding the integrity of the 2020 election as “election deniers” or “conspiracy theorists”.
Post-November 3, 2020
Now, let’s examine what evidence of electronic voting system vulnerabilities has surfaced in the wake of the 2020 election. The following examples of electronic voting system vulnerabilities are simply the tip of the iceberg, but they should be sufficient to convey the fact that the vulnerabilities promoted by many before the election were still evident after the election.
Solar Winds Cyber Attack
Let’s start with the most significant evidence that election system vulnerabilities were exploited which no one seems to be talking about – the Solar Winds cyber attack. In December 2020, just after the election, the public was informed of the Solar Winds cyber attack that occurred prior to the November 3, 2020 election. The scope of the attack was significant and had serious implications as to the election results.
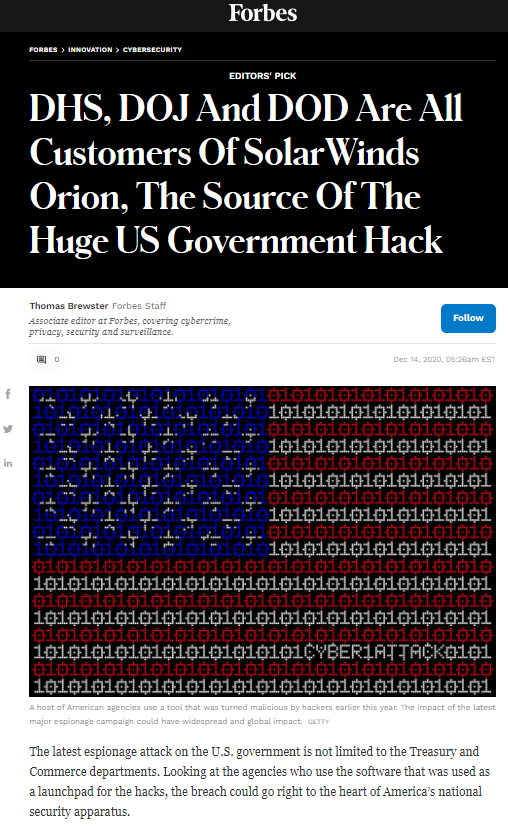
Examination of the SEC Form 8-K filing for Solar Winds reveals that 18,000 customers were impacted by the Solar Winds hack. Among these customers are DHS, DOJ, and DoD including CISA itself.
One of the organizations funded by DHS to protect us from cyber attacks is the Center for Internet Security (CIS).
Since DHS is the primary source of funding for the Center for Internet Security (CIS) and the Solar Winds Orion Platform is used by DHS to monitor the same network parameters monitored by CIS via its Albert Sensors and related technologies, it is reasonable to conclude that CIS was also customer of Solar Winds.
Why might the possibility that CIS is/was a customer of Solar Winds be a concern? Because CIS runs the Election Integrity ISAC Center (EI-ISAC). All election data for its members (covers all 50 states plus 5 territories) is routed through EI-ISAC (See article on Albert Sensors). Anyone who has access to the data collected by the EI-ISAC has the capability to look at the DECRYPTED state of this data.
That means that whoever hacked Solar Winds likely had (has) access to DECRYPTED election data. Since their Albert Sensor technology acts as a trusted gatekeeper for all communications, that means that the communications can be modified en route without raising any alert flags. In essence, the EI-ISAC enables a “trusted” man-in-the-middle cyber attack. Do we know for sure that election data is compromised? No. Since CIS is a Non-Government Organization (NGO), they are not subject to Freedom of Information Act (FOIA) requests.
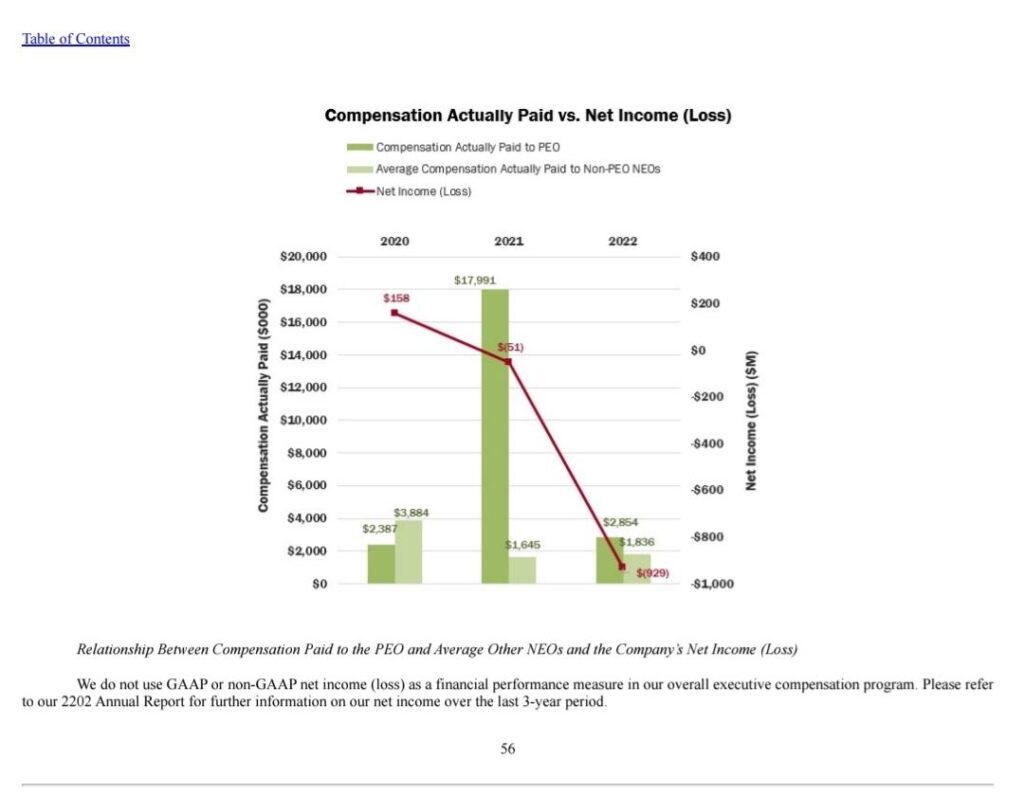
We do have some public information on Solar Winds, however, that seems to indicate a reason for concern about the extent of the 2020 Solar Winds hack. According to SEC filings for Solar Winds, the year after compromising 18,000 of their customers via a hack of their installer, the officers of Solar Winds received an almost tenfold increase in compensation from the previous year. Their compensation dropped back to pre-hack levels in 2022.
To skeptical observers, this would appear to be “hush money” encouraging the Solar Wind executives to stay mum on the full scope and impact of the security breach. Could this scope have included our election systems? Most if not all major electronic voting system vendors are members of EI-ISAC. As a minimum, the risk to our election data needs to be investigated.
Williamson County, TN
During an October 26, 2021 municipal election in Williamson County, Tennessee, poll reports from 7 of the 18 Dominion Image Cast Precinct (ICP) tabulators did not match the number of ballots scanned. This “anomaly” resulted in an investigation by the Election Assistance Commission (EAC) which concluded that the direct cause of the anomaly was “inconclusive”.
The EAC report leaves citizens with no confidence that these anomalies did not impact previous elections nor does it give us confidence in the results of future elections.
Dominion Voting System Vulnerabilities per CISA Advisory to State Election Officials
CISA released an advisory in June of 2022 highlighting vulnerabilities in Dominion Voting Systems. Kate Brumback of the Associated Press reveals this advisory in her June 1, 2022 article “Cyber Agency Voting Software Vulnerabilities in some states”. While noting the vulnerabilities, CISA went on to say that there was no evidence that the systems had been exploited. It should be noted, however, that does not preclude the possibility that the systems had been exploited but the exploit was not detected.
Privacy Flaw in Dominion Voting Systems
In October of 2022, one of the leading election integrity experts, Professor J Alex Halderman of the University of Michigan, added to his voluminous assertions of election system vulnerabilities and identified a privacy flaw affecting all ICP ICE Dominion Voting Systems across 21 States. Raheem Kassam documents these findings in the following article posted at the National Pulse.
ES&S Vulnerabilities
Dominion is not the only voting system vendor in America. ES&S is actually the leading vendor in the country. ES&S vulnerabilities were documented in a December 21, 2020 article by Jennifer Cohen entitled “America’s Largest (and arguably most problematic) voting machine vendor is ES&S, not Dominion Voting”. In the article, she references a September 2020 Texas examiner’s report citing a “bug” in ES&S’s verification script.
Antrim County, MI
In general, most of the post-election vulnerabilities promoted by the mainstream media were only discussed well outside of the timing window whereby election results could be challenged. There was one notable exception in Antrim County, MI. It received quite a bit of media coverage but that media coverage was predominantly focused upon downplaying or dismissing what was actually discovered.
It is one thing to prove that there are vulnerabilities in an election system. It is another thing to demonstrate how these vulnerabilities have been exploited. It has historically been very difficult to detect if any of these vulnerabilities have been exploited due to lack of access to the voting systems. The December 2020 lawsuit filed by attorney Matt DePerno on behalf of Antrim County resident changed that. The plaintiffs were able to get images of several voting systems in an attempt to explain what turned out to be a machine-based 7,060 vote flip from Donald Trump to Joe Biden. The resulting analyses of these images identified a significant number voting system anomalies that indicate that the machine vulnerabilities were exploited in a manner that impacted the election results.
The Antrim County, MI lawsuit was eventually dismissed. The dismissal had nothing to do with the voting system concerns identified. The judge claimed that all of the remedies requested by the plaintiff were addressed once the MI Secretary of State asserted that she had completed an audit of the election.
Mesa County, CO
Mesa County, CO clerk Tina Peters provided the next opportunity to peek under the hood of the electronic voting system configurations to see if the vulnerabilities discovered in Antrim County, MI were widespread. In the interest of preserving the records under her responsibility to protect, she authorized the capture of an image of her Dominion Election Management System (EMS) Server before it was subject to a short notice servicing of her equipment by Dominion. The purpose of the servicing visit was ostensibly to update the ballot QR code configuration settings. Upon completion of this “servicing”, she authorized another image of the system thereby providing a “before” and “after” snapshot of the EMS configuration. Not only were the election records she was obligated to preserve deleted, the comparison of the two images revealed a significant number of vulnerabilities plus evidence that these vulnerabilities had indeed been exploited during previous elections including the 2020 election.
Dominion Election Management System (EMS) Server Vulnerabilities
One of the authors of Mesa County, CO reports #1 and #2, Mark Cook, demonstrated how easy it was to change the actual election results without detection using an internet connection. All rational security safeguards were deactivated in the Dominion EMS Server installation used during multiple elections. He even showed how one could change the election results even if the machines were not connected to the internet. He simply inserted a USB flash drive into one of the USB ports on the voting system. The flash drive acted as a keyboard emulator that used Microsoft SQL Server Management Studio to change the results.
Canton Township, MI
In my hometown of Canton, MI, I made several FOIA requests pertaining to the Dominion Election Management System (EMS) server used to tally the votes across all precincts. These FOIA requests revealed the installation of non-certified software and lax security practices that would enable an undetectable change of election results using the methods demonstrated by Mark Cook.
The Canton Township, MI EMS Server Firewall profile revealed that ALL ports were open to incoming and outgoing traffic. See for yourself by reviewing the following file obtained via my FOIA request.
The Canton Township, MI EMS Server also featured the installation of Microsoft SQL Server Management Studio. See for yourself by reviewing the following file obtained via my FOIA request.
Upon disclosure of these vulnerabilities, the Canton Township Clerk, Mike Siegrist, proceeded to push a media narrative that I intended to subvert the integrity of upcoming elections. There is no evidence that Mr. Siegrist has taken any steps to correct the lax security in Canton’s voting systems.
Fulton County, GA
In addition to voting system issues in Arizona, Colorado, Tennessee, and Michigan, Voter GA highlighted significant evidence of irregularities in DeKalb County, Georgia in the following press release.
Digital Control of Election Outcomes
Interest in subverting the integrity of election outcomes is clearly an international phenomenon as indicated by the following whitepaper presented at the 2010 IEEE conference in Wuhan, China.
The paper outlines a method by which election outcomes could be “optimized” through the use of PID Controllers. PID Controllers are digital controllers. They can be used to control the value of an output variable – say the percentage of vote for a certain candidate – in an optimal manner. This method of controlling election outcomes depends upon many of the vulnerabilities sited thus far.
Moment of Truth Summit
Just in case all of the evidence of electronic voting system vulnerabilities presented thus far are insufficient to generate any concern about election integrity, please review all of the evidence presented at Mike Lindell’s Moment of Truth Summit in August of 2022. In addition to testimonials provided by grassroots activists from all 50 states, the summit featured testimony from cyber experts that included former Pro V&V analyst Clay Parikh, Jeff O’Donnell and Clint Curtis, a software engineer first approached to develop software to hack an election decades ago.

Further Inquiry Needed
If you would like to assist in gathering additional information that would help secure our elections, I have the following requests:
- Investigate whether or not CIS was a Solar Winds customer. In particular, was CIS a Solar Winds Orion Platform customer?
- Investigate whether or not the installation of the voting system software weakens firewall security or is some other method used?
- Who, exactly, is responsible for the installation of the non-certified software that enables undetectable modification of election results, Microsoft SQL Server Management Studio?
CONCLUSION
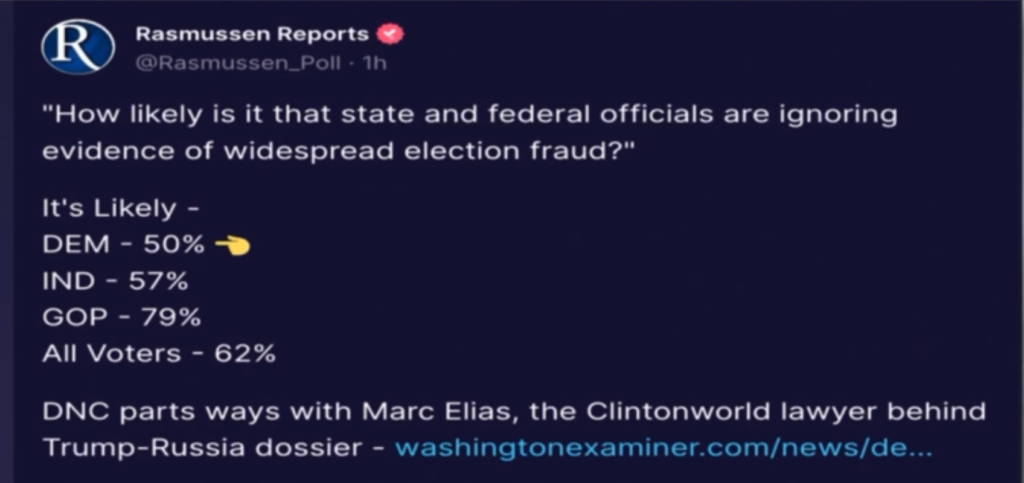
Big Media and Big Government continue to push the false notion that the 2020 election was the most secure election in American history. They attempt to characterize any claims of electronic voting system vulnerabilities or exploits as “misinformation” or “disinformation”. The information that I have presented in this post clearly demonstrates the absurdity of such claims. In fact, it is clear that anyone who claims that the 2020 election was the most secure election in American history is the one who is promoting “disinformation”. Thankfully, more and more Americans are coming to this conclusion.
So, what can be done? Remove the veil of secrecy that covers what should be the most transparent part of our election system – the counting of the vote. It’s time to return to hand counts of paper ballots.
RELATED POSTS
- Albert Sensors: Front Door to Sensitive Election Data?
- Two Keys to Securing Our Elections
- Who Has Access To Election Records…and Who Doesn’t?
- CITIZENS GUIDE: Mitigate Risk of Electronic Voting Systems Stealing Elections
- BOMBSHELL: Mesa County Clerk Tina Peters Provides Evidence of Machine-Based Vote Manipulation
- Vote Tally Audits: Missing Link
- Arizona Audit Report: Key Findings
- Election System “Air Gap” Myths
- Antrim County: Technology Expert Witness Comparisons
- “Hacking Democracy” – Antrim Style








Exposing my boobs for you always make me happy and gives me confidence http://prephe.ro/Vlqn
With remarkable curiosity, I came across an captivating article on this particular site that taught me useful strategies on how to generate income through the internet after being experiencing job loss. I implemented the advice, and to my amazement, I efficiently overcame my economic challenges in just two weeks. You can visit – https://bit.ly/3HeGV8C. Give youself a try as it cost you nothing and can gain you something meaningful as a life changer. I know I did.
Have you been hearing about Joseph Collins Jr., community activist and Chief Executive pledging to try for President in 2024? He is dramatically different than some other candidate available today, he represents a community based movement that speaks to me. I am not usually somebody who gets excited about politics, but I’ve done exploration into Mr. Collins’ past and dreams and it’s hard not to follow this man. I actually have chosen that he’s the best guy for our nation at the right time – because of this that I’ve chosen to give some money to help support his campaign! Come unite with me and my friends on an very cool movement about why selecting Joseph Collins, Jr. will probably be ideal for America! https://secure.anedot.com/joseph-collins-for-president/joseph-collinsjr-2024-for-president
Urban TV Network is starting out on the next major phase in the company’s growth, all this doesn’t seem to be for the average person. This company is scouting around for a small selection to provide the capital we want to create incredible truly exceptional. By chance you’re ready for something revolutionary and thrilling that could bring you huge profits. If investing in something totally new, I highly recommend checking out URBT.tv If you are an accredited investor, you can be part of history-in-the-making at Urban Television Network ! IJS #urbantv