By Patrick Colbeck
You may recall how the Maricopa County officials refused to provide routers or splunk logs to the AZ Senate audit team. After various court actions, the Arizona Senate and Maricopa County came to an agreement that they would jointly designate a “Special Master” to review and answer certain questions posed by the AZ State Senate relating to the conduct of the 2020 general election.
The questions posed are as follows:
- Whether or not there was any evidence that the routers or managed switches in the election network connected to the public internet
- How the routers and managed switches in the election network were secured against unauthorized or third-party access
- Whether the routers or Splunk logs contain any evidence of data deletion, data purging, data overwriting or other destruction of evidence or obstruction of the audit
Download Report by Special Master, Former Congressman John Shadegg
The report was based upon a definition of the “County Network” as represented in the following diagram.
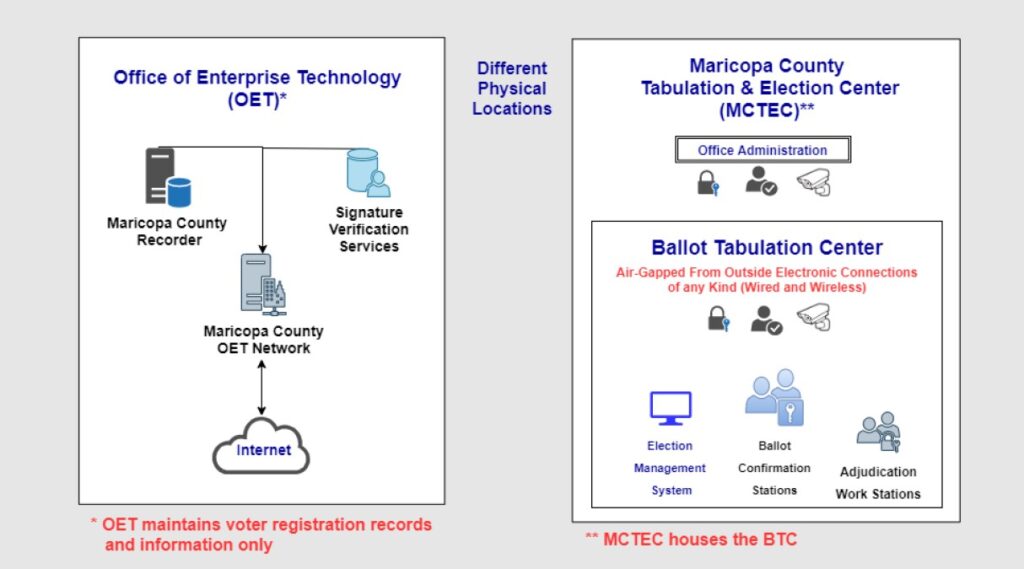
In this diagram, there are two different systems which comprise the “election network” according to the report authors. The first system is the Office of Enterprise Technology (OET). It hosts the voter registration records including original registration forms with the voter’s signature and other information. The second system is the Maricopa County Tabulation and Election Center (MCTEC) and the Ballot Tabulation Center (BTC). The BTC is a supposedly “air gapped” subset of the MCTEC.
Special Master Conclusions
| Question | BTC Response | CET Response |
| 1) Is there any evidence that the routers or managed switches in the election network, or election devices (e.g., tabulators, servers, signature-matching terminals, etc.), have connected to the public Internet? | No. The special master and expert panel found no evidence that the routers, managed switches, or election devices connected to the public Internet. There are no routers or managed switches or Splunk logs in the BTC. | The routers and/or managed switches in the OET do connect to the public Internet. However, the only election related information in the OET is registration information and records. The OET plays no role in the ballot tabulation process, and it is never connected, by wire or wirelessly, to the BTC or to any equipment in the BTC, which is air-gapped from the OET and all outside equipment or systems. No ballot tabulation information is ever received by, sent to or stored in the OET. |
| 2) How, if at all, were the routers and managed switches in the election network secured against unauthorized or third-party access? Is there any evidence of such access? | The special master and expert panel found that there were no routers (or managed switches or Splunk logs) in the BTC. The BTC and the equipment in it are secured by card key access controls and continuous video surveillance preventing unauthorized or third-party access. | The OET is secured from outside physical access by unauthorized personnel by County personnel. The routers and managed switches in it do connect to the public Internet. However, the only election related information in the OET is registration information and records. The OET plays no role in the ballot tabulation process, and it is never connected, by wire or wirelessly, to the BTC or to any equipment in the BTC, which is air-gapped from the OET and all outside equipment or systems. No ballot tabulation information is ever received by, sent to or stored in the OET. Electronic access to the equipment in the OET is continuously monitored by County personnel. Access to registration information has been detected as a result of this monitoring, it was blocked, and the name of the person involved, and the details of the incident were turned over to the Arizona Attorney General for prosecution. Details of this incident appear at item II on page 17 in the Detailed Explanation of Expert Panel Findings. |
| 3) Do the routers or Splunk logs contain any evidence of data deletion, data purging, data overwriting, or other destruction of evidence or obstruction of the audit? | The special master and expert panel found no evidence of data deletion, data purging, data overwriting, or other destruction of evidence or obstruction of the audit. | The special master and expert panel found no evidence of data deletion, data purging, data overwriting, or other destruction of evidence or obstruction of the audit. |
In summary, they concluded that since there were no BTC routers or managed devices, there was no “public internet” connection and therefore no information worth capturing related to Splunk logs.
Key Terms
The report repeatedly emphasized the following terms:
- Public Internet: Is this intended to assert there were no TCP/IP connections of any sort?
- Air-Gapped: Is this intended to mask the existence of VPN or firewalls to secure TCP/IP connections?
- Tabulation Equipment: Is this intended to create impression that tabulators were not connected to any other peripherals which may have had vulnerable TCP/IP connections?
Their use of these terms begs a few follow-up questions.
Recommended Follow-Up Questions
- How do you define “public internet”?
- How do you define “air gapped”? Many technology vendors assert that there is equipment is “air gapped” merely because they use a VPN or firewall. These security measures are still vulnerable to intrusion by interested third parties.
- How do you define “tabulation equipment”?
- How did the BTC equipment receive election results from the precincts? Is there verified log data or other evidence which validates this assertion.
- Was the EMS server connected to any other devices? If so, what devices? How were they connected?
- How did the EMS server receive software updates? Who administered these updates and when? What evidence is there to support these assertions?
- Were any wireless devices installed on the EMS server? In Mesa County, CO, 36 wireless devices were found connected to the EMS server.
- Were any TCP/IP connections evident for election equipment in the BTC?
- The Dominion D-Suite is installed on a Windows-based platform. Did anyone review Windows logs such as the event log or resource monitor for evidence of TCP/IP connections?
- Was any equipment in the BTC connected to any other equipment in the BTC? If so, how?
- Was any equipment in the BTC connected to equipment in the MCTEC? This equipment does not have to be election equipment. It could be a printer or scanner or even a thermostat as evidenced in Georgia.
- What are the names of the County personnel who continually monitored the access to electronic equipment in the OET? Is there evidence which validates this assertion? How did they monitor the access to electronic equipment?
- Were there any Dominion support calls made from the BTC in support of the 2020 election? When? How was each support request resolved?
- How do their claims reconcile with evidence provided by forensic experts such as Ben Cotton which provided evidence of internet connections?
…and that’s just for starters.
Conclusion
The Special Master report is remarkable in its lack of details. It appears that they are attempting to play the same word games in this report that are used by vendors to convince election officials that their systems are “air gapped”. The authors of the report appear to be focused upon assuaging the letter of the questions asked as opposed to assuaging the security concerns behind the questions. Without receiving answers to the recommended follow-up questions, I do not believe it is reasonable to conclude that there were no connections to the internet – public or private.
Related Stories
Election System “Air Gap” Myths
BOMBSHELL: Mesa County Clerk Tina Peters Provides Evidence of Machine-Based Vote Manipulation
Arizona Audit Report: Key Findings