By Patrick Colbeck
Election officials all across the nation are being treated to a plethora of security jargon from electronic voting system vendors intended to convince them that the data connections for their voting equipment are secure. Here’s a sample of vendor jargon to be on the watch for:
- “Your data is transferred over a cellular network”
- “The system is not connected to the internet…during tabulation”
- “We have a firewall”
- “Your data is encrypted”
- “We use secure VPN technology”
- “Your system is air gapped”
Such vendor claims often result in claims by election officials that they are “not connected to the internet”. But is that true? In general, no. Why? Everyone of those responses imply that the voting system IS connected to the internet. They simply attempt to hide that fact with security jargon.
No one can deny that during an election cycle there is a transfer of election data from precinct-level tabulators to results aggregation systems at the municipal, county, and state levels.
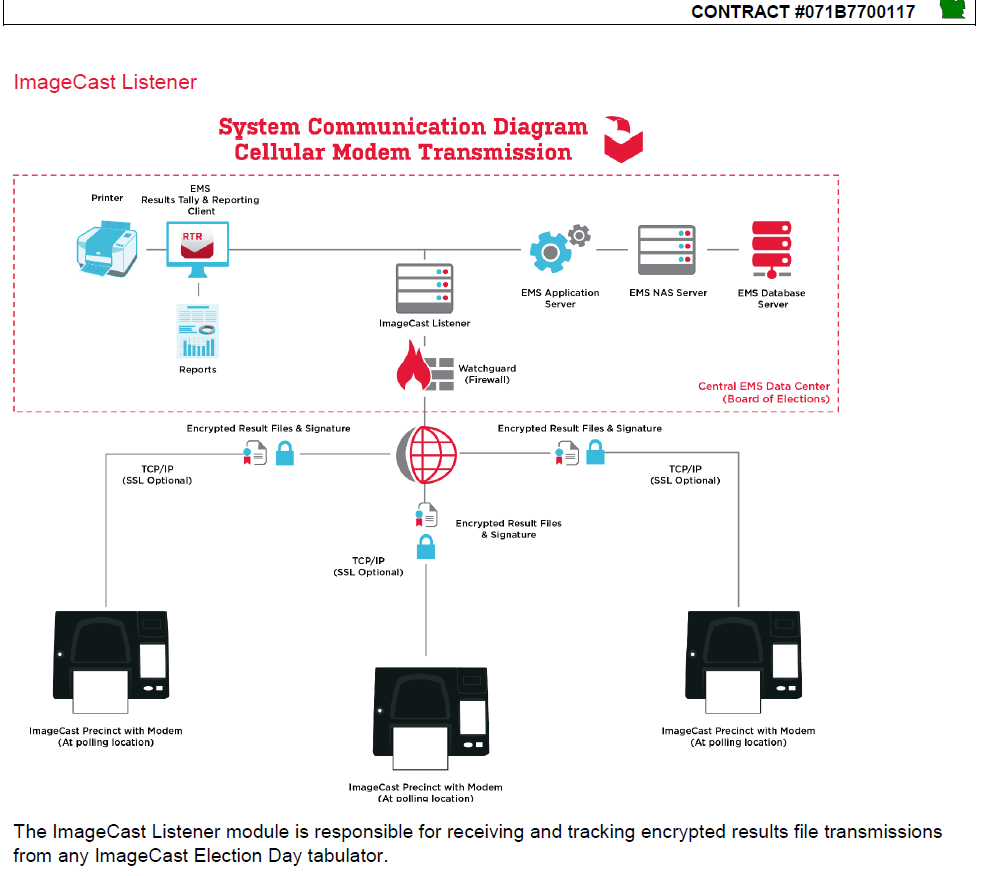
The fact remains that the security of any electronic voting system and, therefore, the security of the election record chain of custody is vulnerable at any time between the time the election equipment (hardware, software, network configuration) is certified and the election itself is certified. If election officials are unable to validate the security of their voting system configuration during that time, any election data transferred during that period may have been compromised.
This begs the question is “how is election data transferred?”
DATA TRANSER METHODS
The following data transfer methods are typical:
- “Sneakernet”
- USB-compatible cellular modem
- Ethernet connection
- Wireless modem chip embedded in motherboard of voting machine
Sneakernet
The “sneakernet” method of transferring data refers to the physical transport (i.e. by someone in sneakers) of removable storage media (e.g. Compact Flash Card) from Point A to Point B.

There is no network connection of any sort involved in this method of data transfer.
USB-compatible cellular modem
Many municipalities use “USB-compatible” cellular modems.

These modems are typically only inserted once the election results have been tallied and the precinct workers are prepared to submit their certified results to the local clerk’s office.
Ethernet connection
Many electronic voting systems feature ethernet connections featuring Cat 5, 5e or 6 cables.

These connectors are plugged into ethernet cards installed on voting equipment. The other end of the ethernet cable typically connects to a router or managed switch which in turn forms a Local Area Network with other voting equipment. If any device on this Local Area Network is connected to the internet, all of the devices will typically have an internet connection or at least be vulnerable to the establishment of an internet connection.
Wireless modem chip
Not all data transfer mechanisms are visible to the untrained observer. Wireless modem chips have been installed on the motherboard in some electronic voting systems. These chips are hidden from the casual observer by the equipment chassis. Even if the chassis were to be opened up, it would take someone familiar with motherboard and chipset design to identify the existences of a wireless modem chip installation.

The installation of a wireless modem directly upon the motherboard is the equivalent of connecting a modern smartphone to your voting system. As soon as the equipment powers on, it says “hello internet”…many times without the clerk’s knowledge.
Out of all of these connection methods, only item 1, “Sneakernet”, is truly air-gapped. All of the others involve connections to an internet backbone.
WHY IS INTERNET CONNECTIVITY BAD?
What can happen if voting systems are connected to an internet backbone? Cyber attacks. What kind of cyber attacks?
Man in the Middle
A “Man in the Middle” attack involves the clandestine diversion of data intended to be transferred from Point A to Point B to an intermediate Point C before the data reaches Point B.
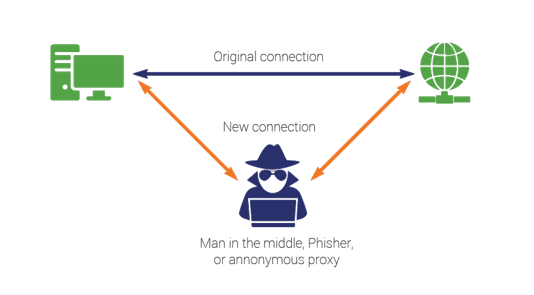
Point C could insert changes to vote tallies or poll book data designed to modify election results without detection.
Malware Insertion
Malware features instructions intended to subvert the operation of an electronic voting system. Malware is most commonly installed as software instructions but could also be embedded in hardware as well.
Malware can be embedded in a system via the internet or by anyone with physical access to the voting equipment. It can be very difficult to detect. Voting systems are vulnerable to malware at any time between the certification of the voting equipment and any equipment connected to it on its network (e.g. printers) and the certification of the election.
Surveillance
Surveillance involves the sharing of election data such as vote tallies or voter status. Many municipalities share “unofficial election results” prior to the closure of voting precincts. These “unofficial election results” help satisfy the public desire for speedy election results but they also provide nefarious actors valuable information that can be used to determine how many ballots for their candidate must be “stuffed” into ballot boxes before precincts are “closed”.
HOW CAN I SECURE AN INTERNET CONNECTION?
Can internet connections be secured? Yes, but they are never 100% secure. VPN’s and firewalls are often cited as the best tools for securing data communications, but they have significant security vulnerabilities that need to be addressed.
VPN’S
How does a VPN secure data connections?
- Encryption
- Mask real IP address
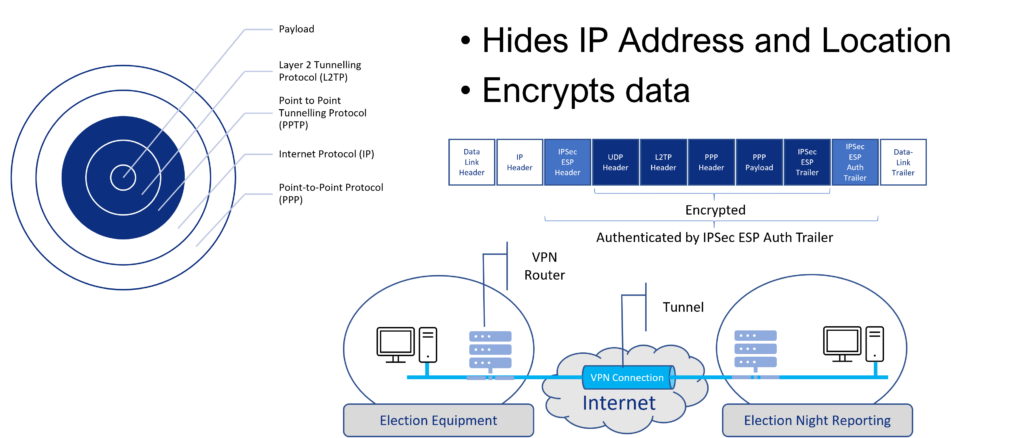
Can a VPN be hacked? Yes.
Key questions to ask of election officials leaning on a VPN to secure election data:
- Who is VPN service provider?
- Where is VPN service hosted?
- Who has access to encryption key?
FIREWALLS
How about firewalls? Can you bypass a firewall and access the network it protects?
Firewalls control what ports are open, monitors traffic through those ports, and blocks ports to which you seek to deny traffic.
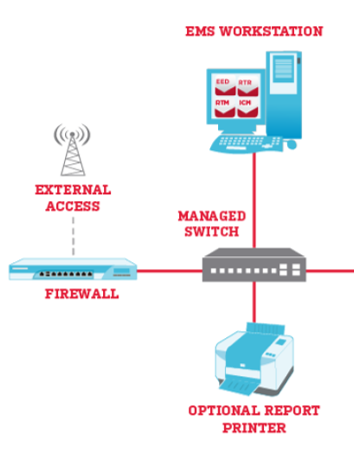
Can you hack a firewall? Yes. Don’t take my word on it though. This is what the experts say.
Hopefully, this brief overview of internet connections provides sufficient clarity as to why internet connectivity in conjunction with election equipment calls into the question the security of the election record chain of custody.
QUESTIONS FOR ELECTION OFFICIALS:
If your election official insists their voting system is “air gapped”, I encourage you to ask them the following questions:
- What standards do you use to certify the software configuration of your voting machines?
- Who verifies compliance of the software configuration for each machine with these standards? When?
- Would you classify the installation of non-certified software on election equipment as an “irregularity” that needs to be investigated?
- Are you aware that multiple technical experts discovered the installation of SQL Server Management Studio on Antrim County election equipment?
- Are you aware that SQL Server Management Studio is not part of the Election Assistance Commission certified software configuration?
- Are you aware of why this software is not allowed as part of the certified software configuration? Do you know what functions it is capable of?
- Do you believe that the installation of non-certified software capable of changing election results would be grounds for decertification of the election? If not, what do you believe is the appropriate criteria for the “certification” of an election?
- What standards do you use to certify the hardware configuration of your voting machines?
- Who verifies compliance of the hardware configuration for each machine with these standards? When?
- Do you connect any of your election voting equipment to any any other electronic devices during the period of time between the software and hardware certification of your machines and the certification of the election results? If so, by what means (e.g. Wi-Fi, Ethernet, 3G/4G Modem)?
- Are your communications encrypted? If so, who controls the encryption keys used?
- Do you have a list of all of the IP and MAC addresses for all election equipment and connected network devices used during the election? If not, how do you secure the chain of custody pertaining to electronic voting records if you do not know what devices have access to those records?
- Do you have a record of the connection settings for any applications transferring data to external networks? Do you know with absolute certainty whether or not these connection settings allow for two-way data transfers? If so, how do you know?
- Have you completed a software audit of all devices connected to your election voting equipment? Hardware audit? If not, why not? If so, when? How?
- Do you connect any of your election voting equipment to election equipment at municipal offices? County offices? State offices? By what means?
- Do you have access to traffic logs for all of your network devices (e.g. routers)? Where are these logs stored? How are they secured?
- Do you believe that if any one of these networked devices are compromised, the election record chain of custody is compromised?
- Have you been told by vendors that your voting systems are “air gapped”?
- If so, what proof were you provided of this assertion?
- Are you aware of the discovery of a 4G Wireless modem being found installed on the motherboard of an ES&S 200 voting machine? (i.e. every time the machine was turned on, it was telling the internet “here I am”)
- Are you aware that there is evidence of this device communicating with foreign servers (Taiwan, Germany) during the election cycle?
- Does it concern you that there is evidence of foreign communications with our election system?
- Have you inspected the motherboards for your voting systems to preclude the existence of any wireless modems?
- Do you drop off your equipment to third party vendors for “maintenance”?
- Do you certify the configuration of your equipment before drop off and upon return? If so, how do you certify the configuration? If not, how do you verify that the chain of custody for the election has not been subverted as a result of configuration changes made by your vendor or parties to which the equipment was shipped out by vendor?
- Do you have the administrative account credentials for your election management system?
- Do you have the administrative account credentials for all electronic devices within your jurisdiction (e.g. servers, laptops, routers)?
- Do you have the administrative account credentials for any database management software used to support election management?
- Do you share your administrative account credentials between personnel or does each individual have their own account credentials?
- When was the last time you changed your account credentials?
- Do any vendors have administrative account credentials for your voting equipment? If so, have you ever conducted an audit of their administrative activity on your election equipment?
Do you believe that your election officials are ready to answer the questions above? If not, how can they or anyone assert that the 2020 general election was the “most secure election in history”?
CONCLUSION:
Until such time as the vast majority of election officials can provide substantive answers to the questions posed above, ALL elections should be devoid of electronic voting systems. In the final analysis, the only voting systems guaranteed to have an “air gap” are manual systems that we used prior to electronic voting systems.
RELATED STORIES
Modem Chips Embedded in Voting System Computer Motherboards
Election Fraud Evidence Primer



Keep up the good work Patrick! You’re an inspiration to us!
Wait, so you complain about air gaps, then do not address them.. then complain about configuration changes but also complain about random local officials being unable to change configurations. This.. does not seem intellectually honest and shows a very grade school level understanding of how communication systems work. I am trying to figure out if the poster is ignorant, or intentionally misinforming people.
I found SQL 2008 listed on the MI Dominion contract, which comes bundled with Server Management Studio as of 2012. Would this not mean that SQL SMS is certified?
I’m still watching the symposium, but am so excited. Thank you!
Patrick.
My wife of 60 years and I have been residents of Oakland County since 1966 except for two years in Potomac MD. I want to do all I can to get a forensic audit underway ASAP in MI.
Lisa Brown is our Oakland County Clerk, How do I move the effort forward?
One thought, would it be worthwhile to get records of the 2020 presidential and senatorial vote for our precinct of Southfield Twp? If I found discrepancies between what our precinct forwarded and the County’s records, I could show it to our Twp and our Village of Beverly Hills so that I might get citizen support.
This is just a thought. I am a decent analyst and would be glad to assist in any way. I met you earlier at the Lakes meeting in Walled Lake and greatly appreciate your leadership.
John “Jack” McGrath
Thorough and complete explanations in easy to understand language!