By Patrick Colbeck
Good clerks all across America insist that the 2020 election was a secure election. In support of their assertions, they often affirm that they followed all election procedures to the letter. To the skeptical mind, however, it begs the question, “Do our current election procedures protect us from election fraud?”
When I was a young design engineer working on the Space Station program, I took a good deal of pride in the subsystem I designed as part of the station’s Environmental Control and Life Support System. I was confident it would work as designed. All the astronauts needed to do was follow the operations guide provided for the design. At least I was confident until I met with another group of engineers focused upon safety and reliability. They asked me a series of disconcerting questions like “what if this happens?” or “what if that happens?”. My confidence in my design began to waver. I began to realize that changes would need to be made. Rather than mope around in denial, I made changes that would mitigate the probability or impact of the risks which the “what if” crowd posed to me in our design reviews. Their insights made my design better. To the best of my knowledge, the systems that I designed with the assistance of the “what if” crowd are still working in orbit above the Earth well beyond their original design life.
Why do I share this blast from the past? Because I believe we need to go beyond the complacency that comes from following a procedural script for the conduct of our elections. We need to recognize that there are quite a few “what if” scenarios that are not only highly likely but also would have a severe impact upon our election integrity. There are also quite a few bad actors in the world around us who would like for nothing better than to convert our “election” system into a “selection” system.
How do we protect ourselves from these bad actors? Follow the lead of the Space Station “what if” crowd and map out all of the possible ways our election system could be subverted. That’s exactly what I’ve attempted to do in the following process diagrams.
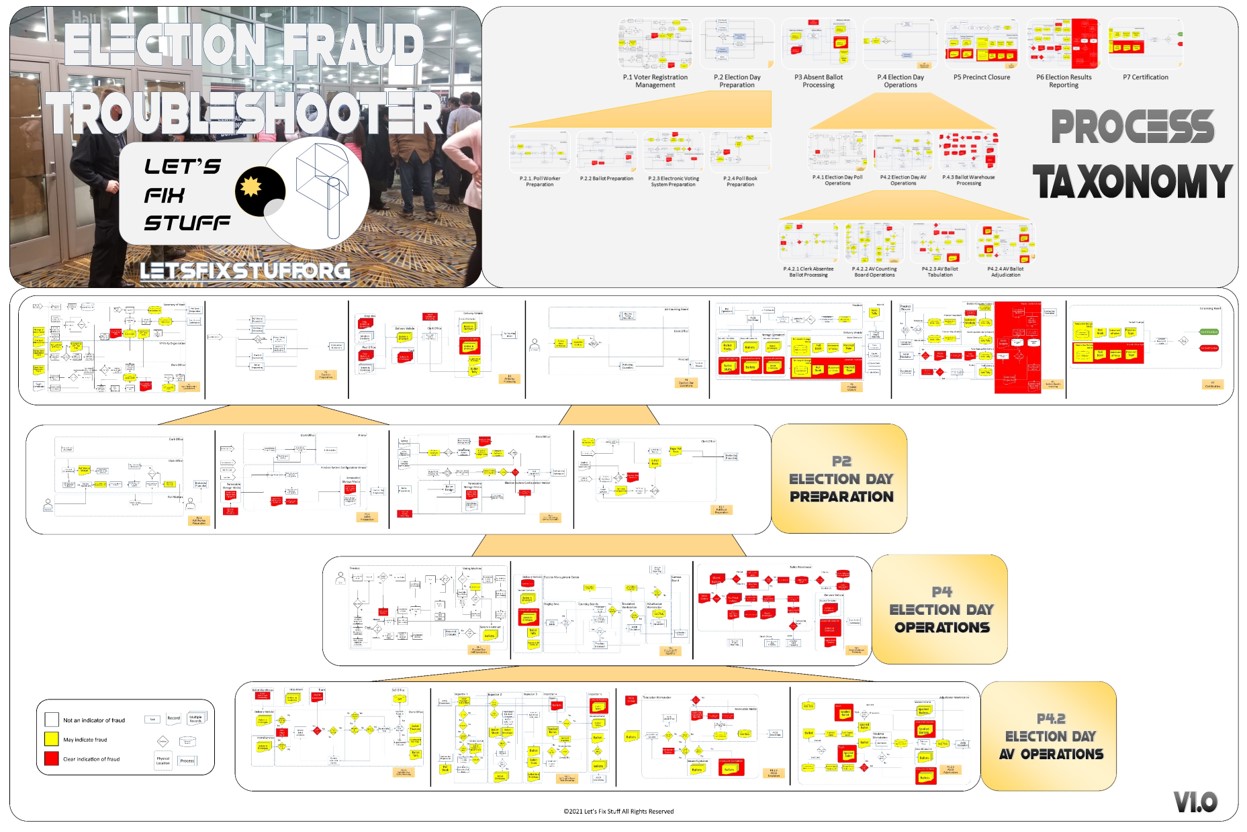
Election Process Taxonomy
My work on a comprehensive election process taxonomy started with my assignment as Vice Chair of the Michigan Senate’s Elections and Government Reform Committee back in 2015. I interviewed clerks and state election officials as well as read election manuals to develop my first cut at a view of how elections are supposed to work.
During the 2020 election, after I was term-limited from service in the MI Senate, I served as a Poll Challenger at the TCF Center in Detroit. It inspired me to expand my process understanding beyond how it is supposed to work to also address all of the ways that the election processes could be subverted either inadvertently or deliberately. The result of this effort is the following process taxonomy.
How To Use
This process taxonomy can be used in many ways but the primary ways are:
- Develop a Concept of Operations as to how election was subverted so as to guide investigations
- Provide an audit roadmap with sufficient detail to readily identify specific fraud evidence
- Provide a framework by which lawmakers can assess the effectiveness of current election law statutes
About a week after my experience at the TCF Center in Detroit, I sought to compile a Concept of Operations intended to be posted on a War Room wall somewhere in DC. It never happened, but I didn’t give up on the pursuit as you can see.
This map can still be effective as an audit roadmap. The primary purpose of audits is to ensure process compliance. In order to ensure process compliance, one first needs to define the process. Furthermore, one needs to have the process defined with enough specificity to preclude fraud. In this context, auditors can map their election observations as follows:
- If there are audit findings that can be binned in red blocks, fraud has been committed.
- If there are audit findings that can be binned in yellow blocks, fraud may have been committed. A forensic audit will help determine if it has been committed or not.
- If you no findings suitable for red or yellow blocks, you can breathe a sigh of relief.
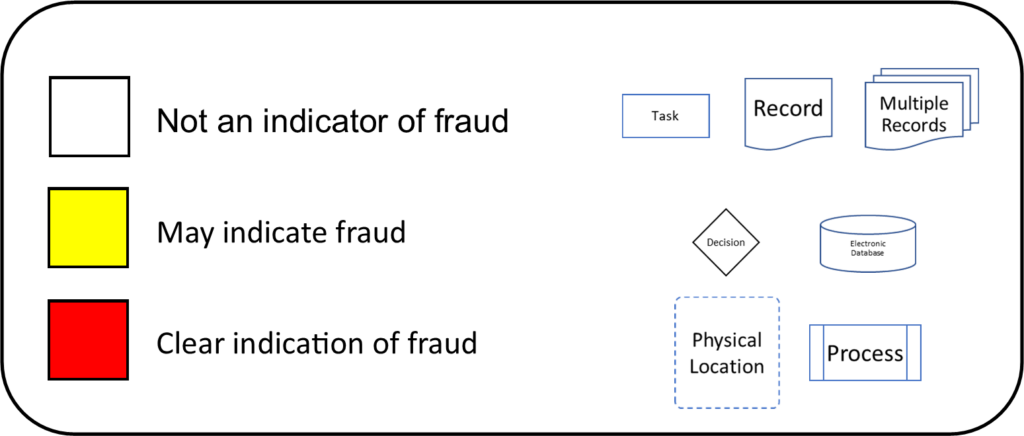
Last of all, legislators can use the process taxonomy to identify gaps in current election law. If there are insufficient protections in current law to preclude any items in red from being discovered or prosecuted, laws should be put in place to fill that gap with sufficient penalties to discourage any subversive behavior.
Process Maps
In order to facilitate examination of the Version 1.0 Election Fraud Troubleshooter Process Diagram, it has been broken down section by section for your review. There are 7 major process groups. Some of these groups are in turn broken down into more detailed sub-processes. You can use the Process Map ID (e.g. P4.2.3) to help you keep track of where you are in the overall process taxonomy. The processes are intended to be generic enough to apply to multiple states, but there may be Michigan-specific terms that may need to be translated state-to-state (like “pop” vs “soda”).
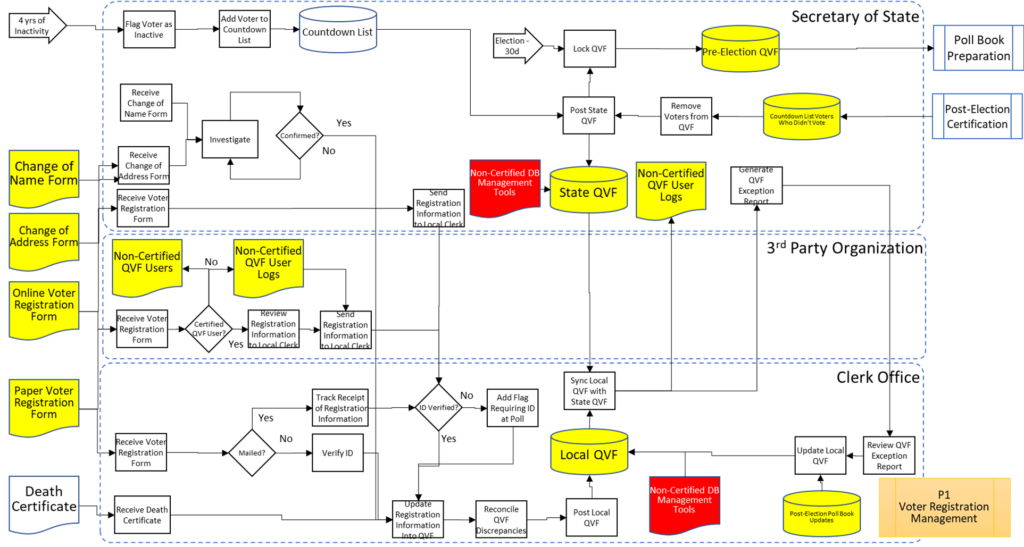
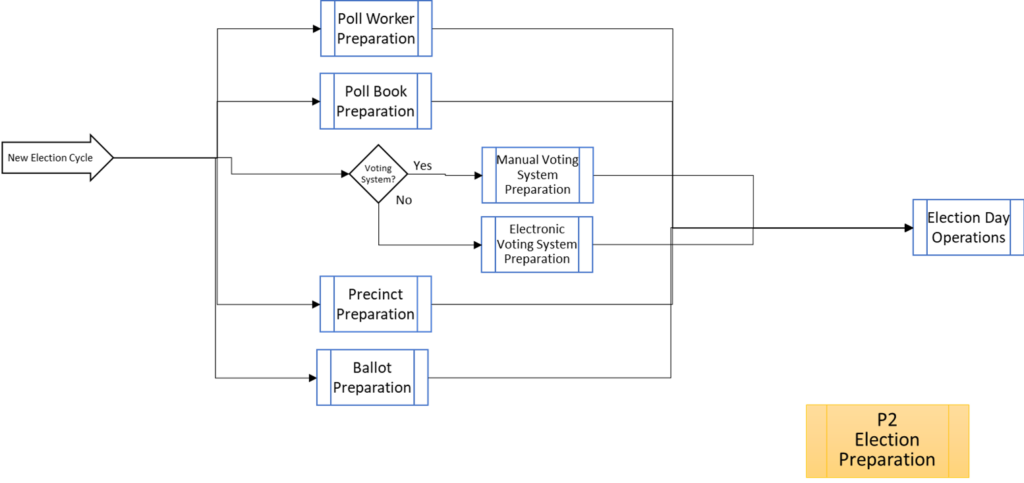
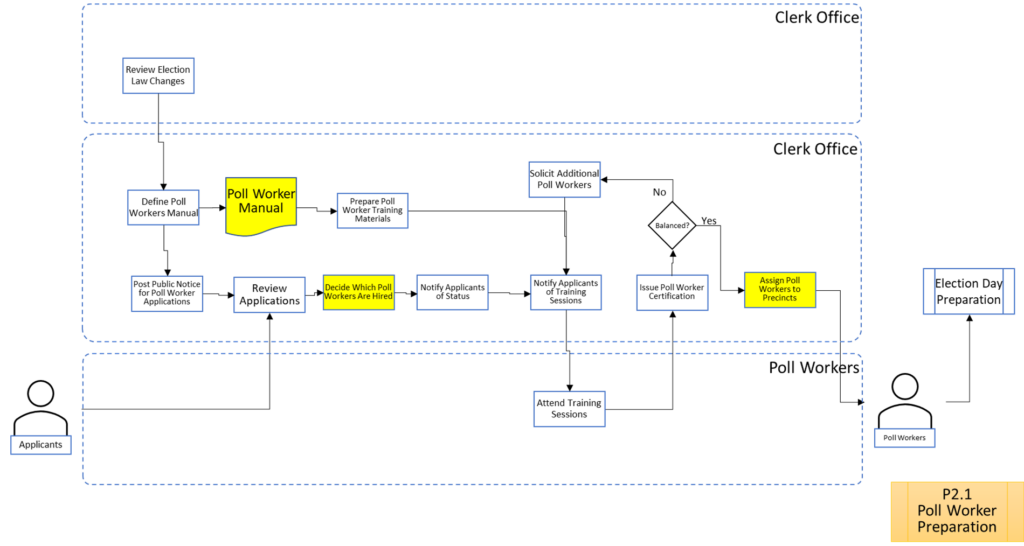
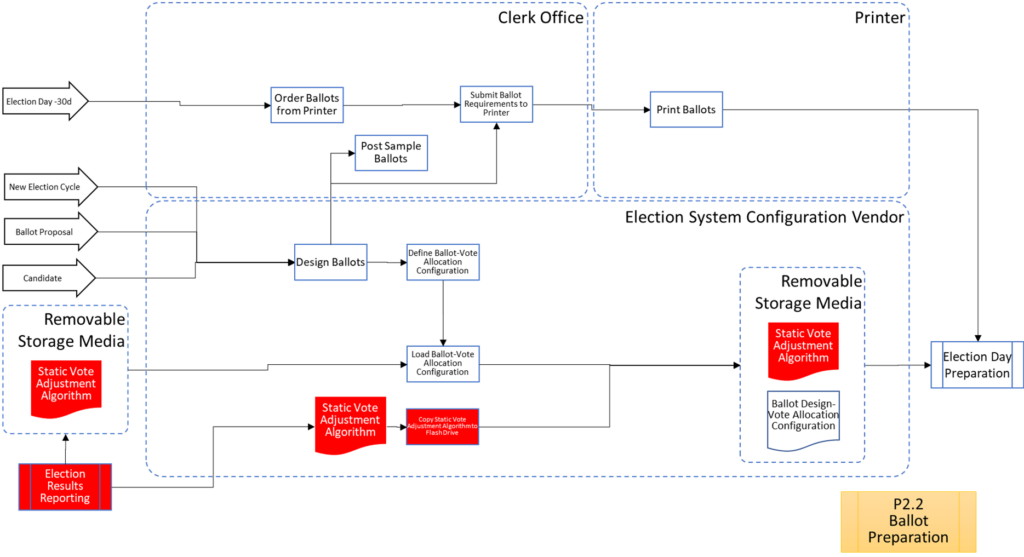
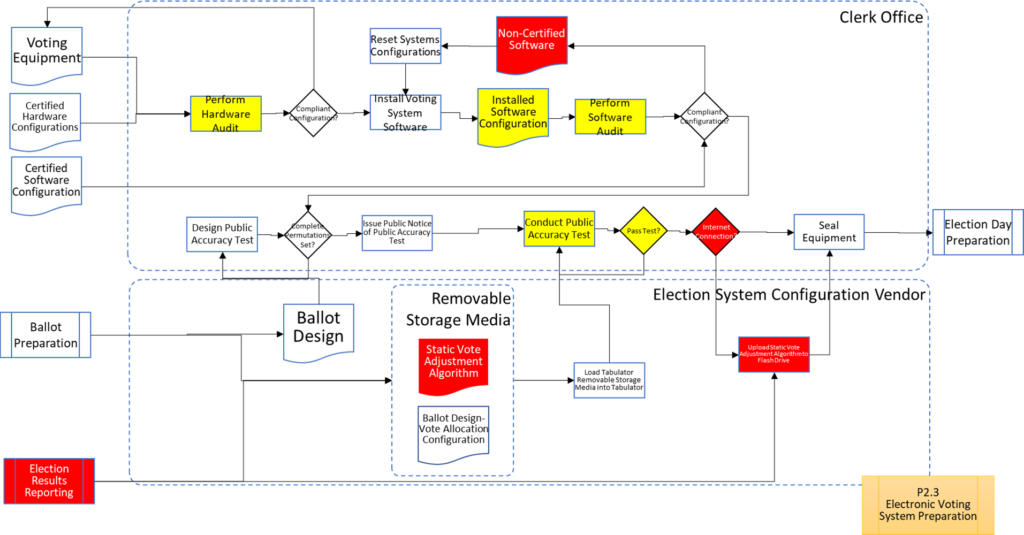
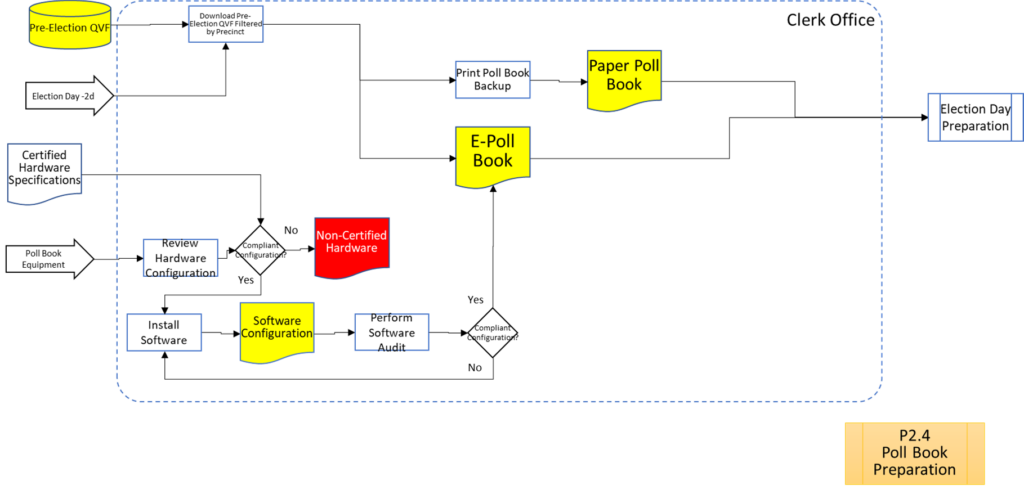
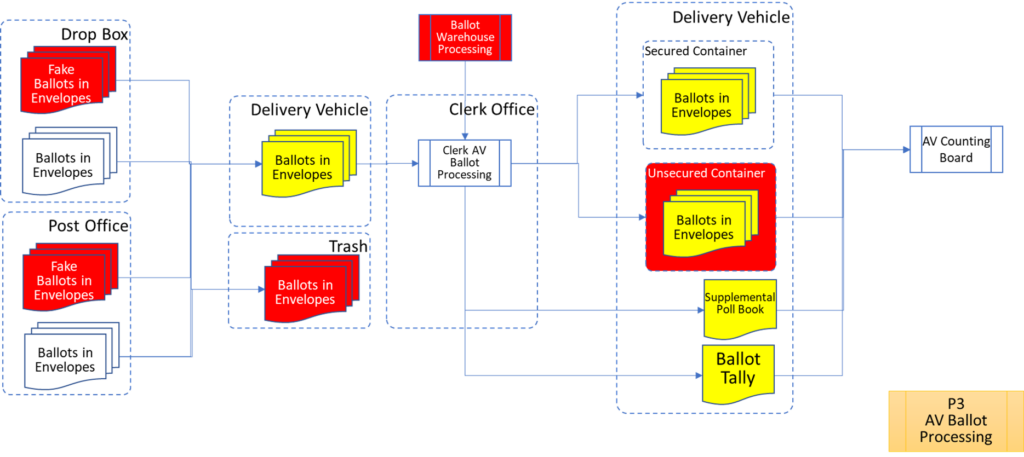
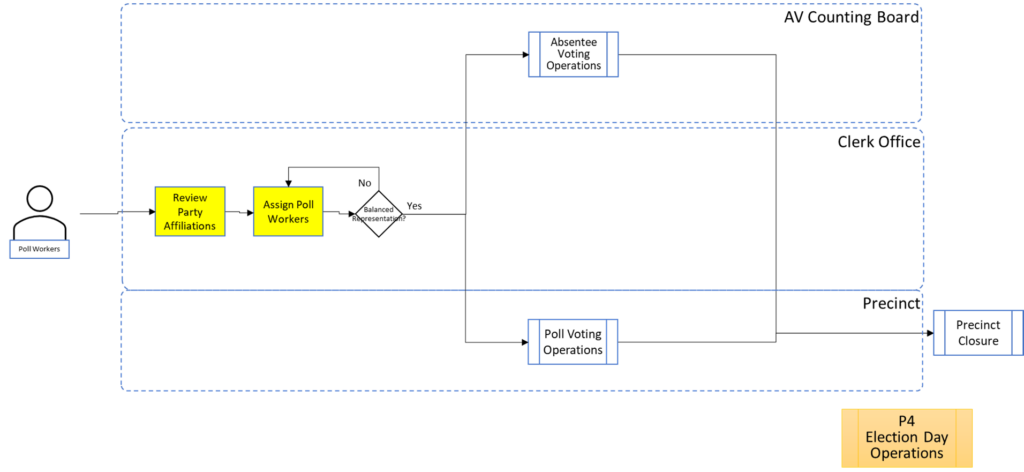
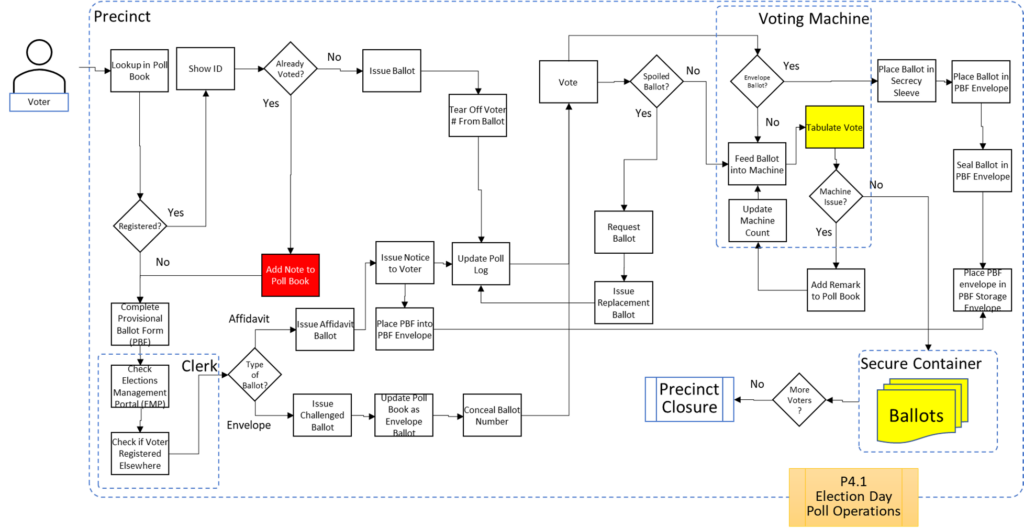
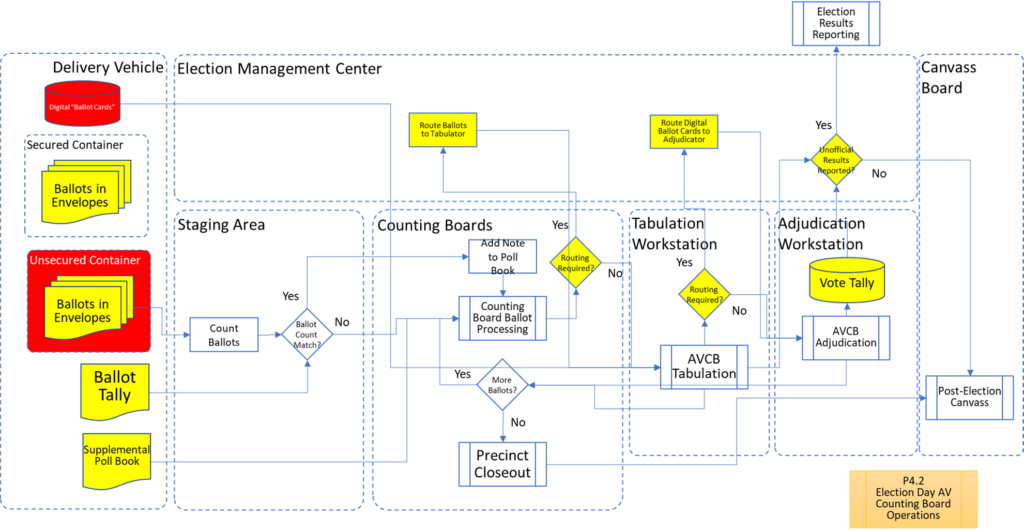
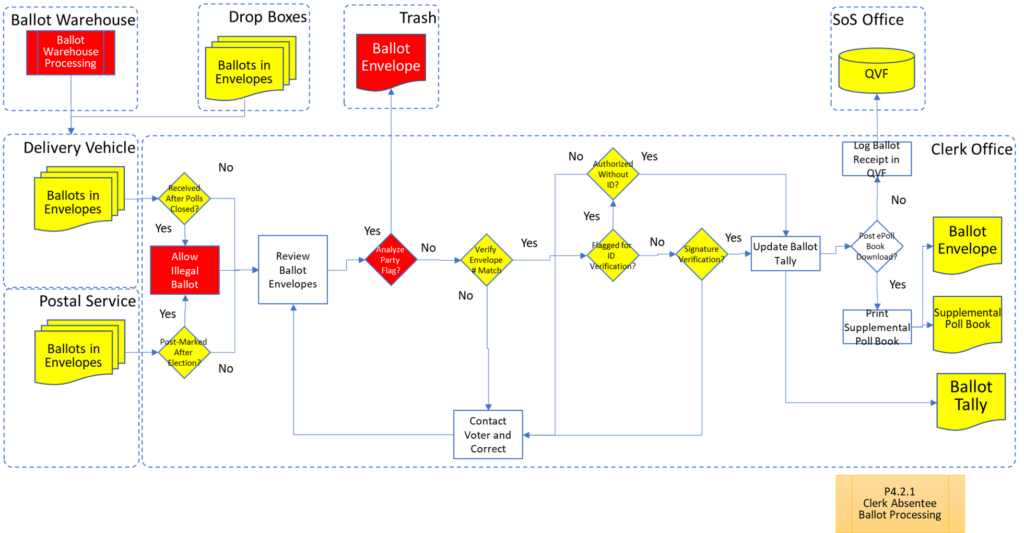
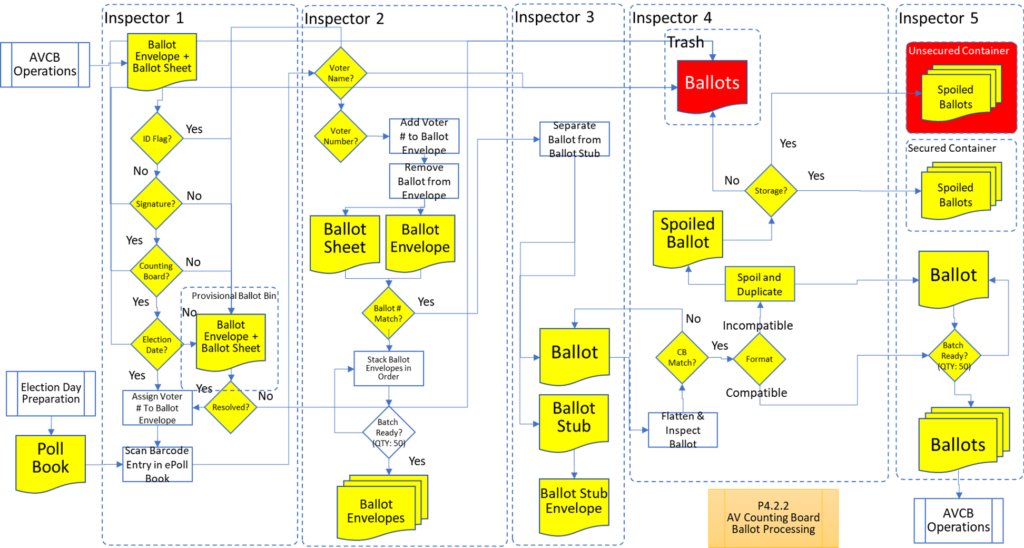
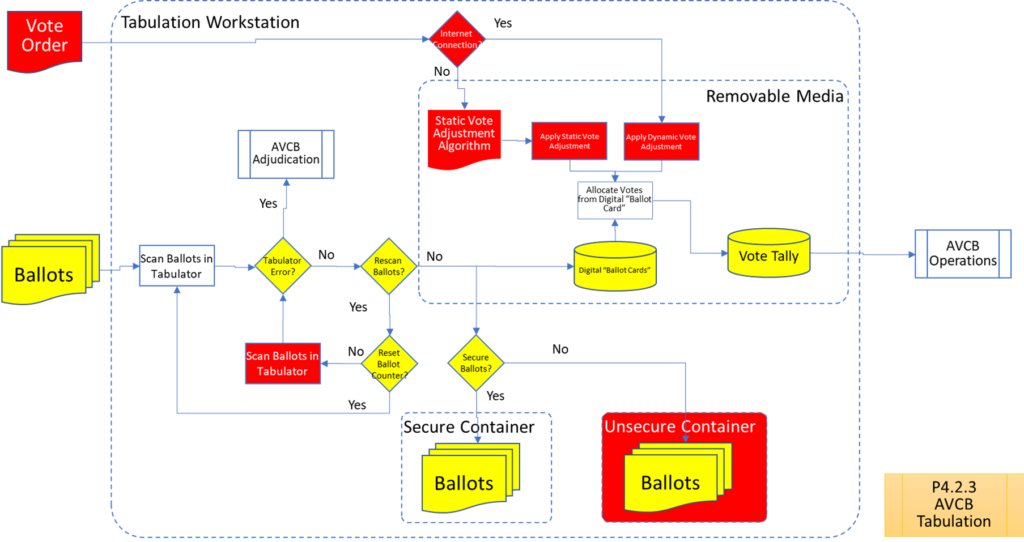
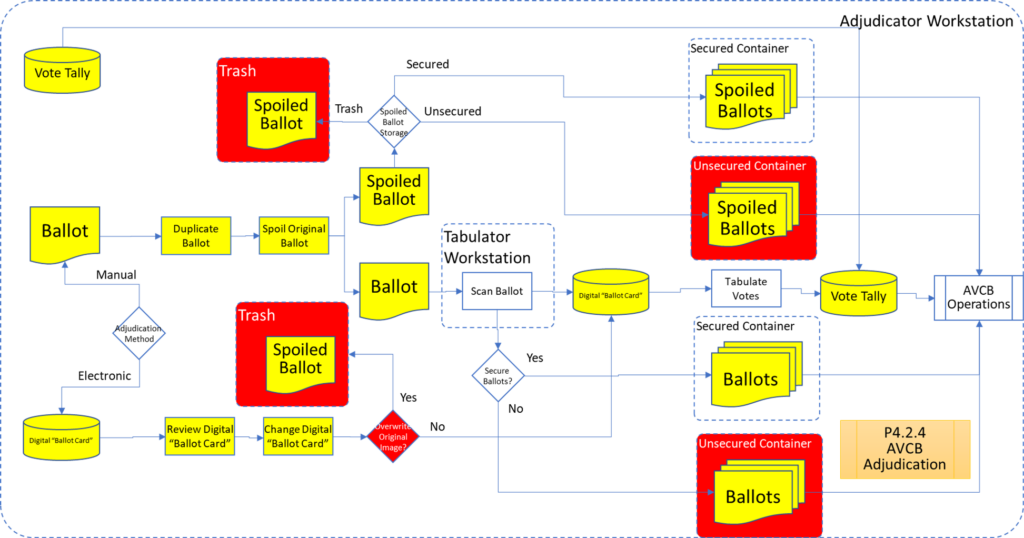
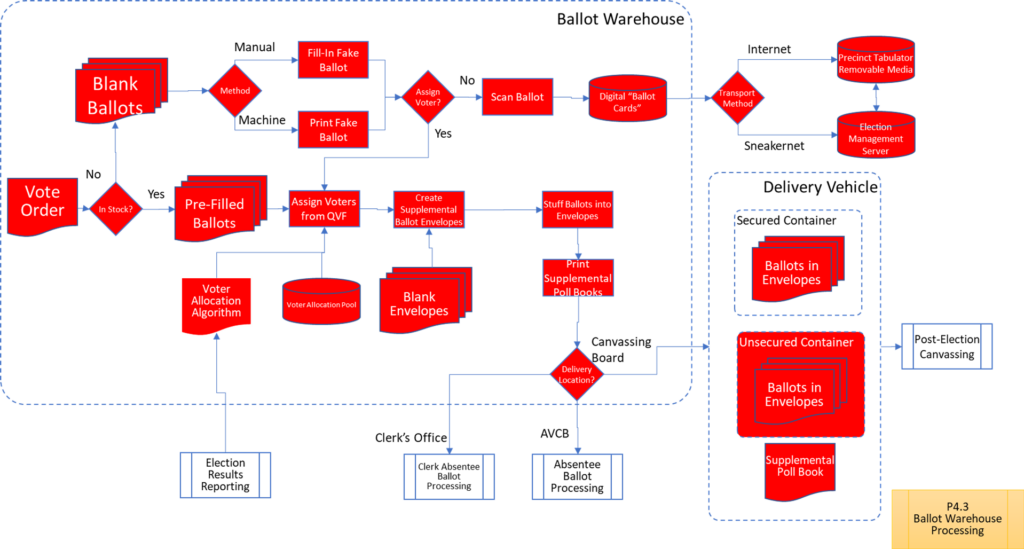
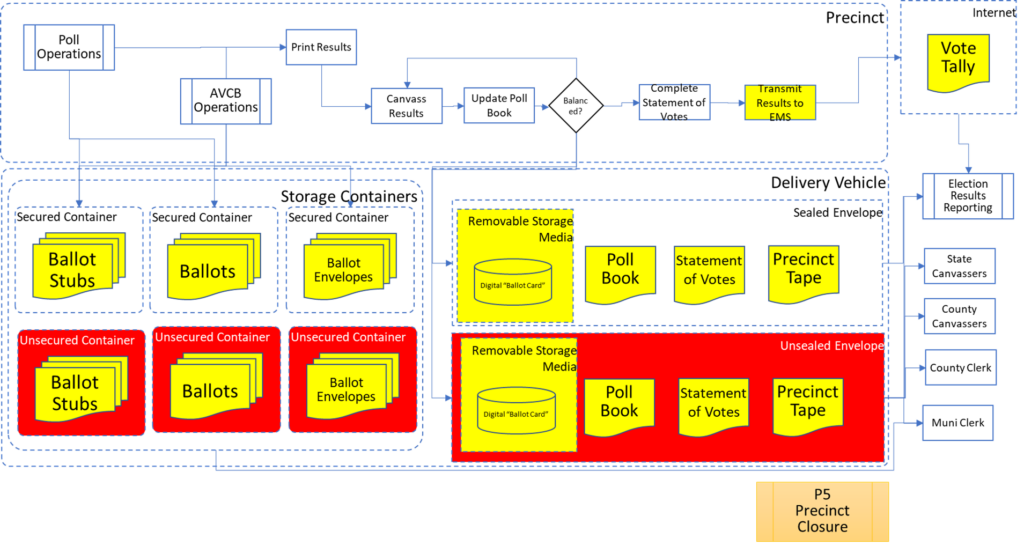
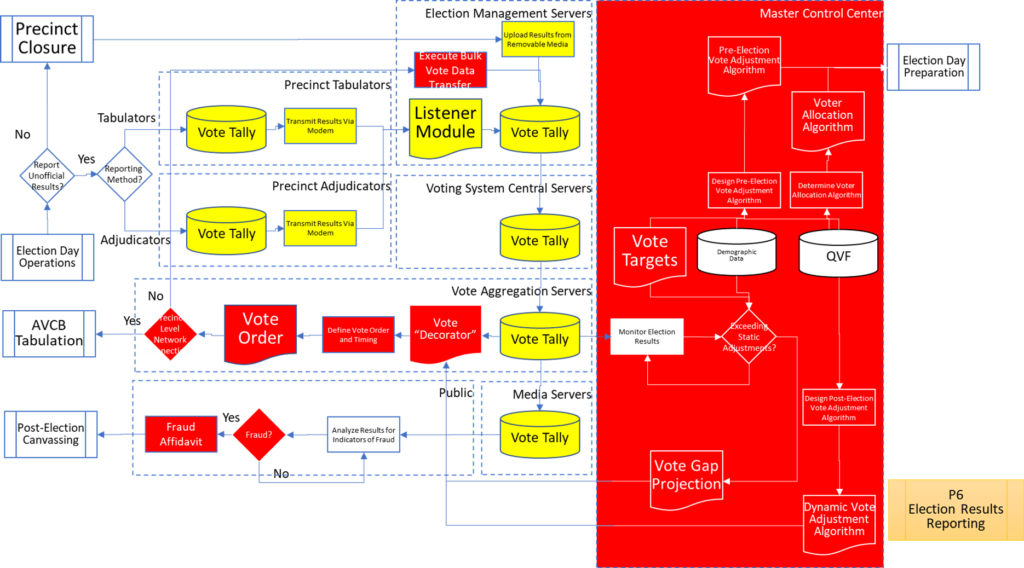
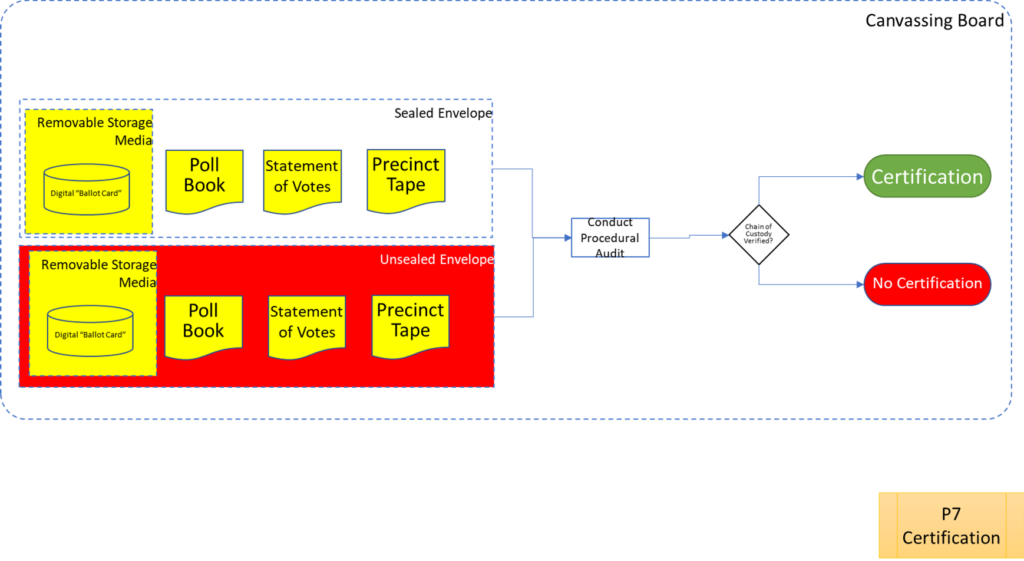
That about wraps it up. With these process maps in hand, you are equipped to be an effective defender of the integrity of our elections.
Next steps?
I am in process of mapping all of the 2020 election fraud evidence that I have to the blocks in these diagrams. This is tedious work, but worth the pursuit.
SPECIAL NOTE:
The process taxonomy that I’ve compile is labelled “Version 1.0” for a reason. If you see mistakes or missing elements, please share your comments to [email protected].
Thank you!
Patrick Colbeck


Who can I get in touch with to protest this mask mandate and fight these election fraud criminals in my STATE?????
I need assistance in finding a support group in Kansas to get the attention of our election officials. My local election office needs direction to do the forensic image from “those in charge”. I have found a local certified forensic expert who is very willing to do the imaging, but need more help. I have left messages at the home phones for Randy Garber – the Kansas Rep who was at the Cyber Symposium and my local rep, Renee Erickson. The KS legislature is not in session. Who else should I contact?
There is an audit group on Telegram for each state. They should be helpful.
There are various groups in MI gathering “grass roots support” for a forensic audit. All of your work should be used to specify the scope of work in such audits. Our best example so far is AZ. Many people in Blue states claim that auditors are partisan(Republican). Just as there are poll watchers, the opposition should be allowed “audit watchers”. Than we may have to deal with leakers and disrupters masquerading as audit watchers! Security in this process must be paramount.
Is this diagram down-loadable? Would like to print out and distribute