By Patrick Colbeck
Growing up, many kids have played the game “Telephone”. In Telephone, kids form a circle. Then, one of the kids whispers a message into the ear of the kid next to him or her. Then that kid proceeds to whisper the message into the ear of another kids and so on until the “original” message finally reaches the kid who started the “telephone call”. If the message that the originator hears after the messages has been passed around the circle is the same one they initiated, the kids were successful in maintaining the integrity of the message.
In order to maintain the integrity of any election, we need to execute an adult version of telephone involving the maintenance of an Election Chain of Custody.
What is an Election Chain of Custody?
In order to execute elections with integrity, there are many links in the chain of custody. I’ve put together a rough sequence of these links in the following diagram.
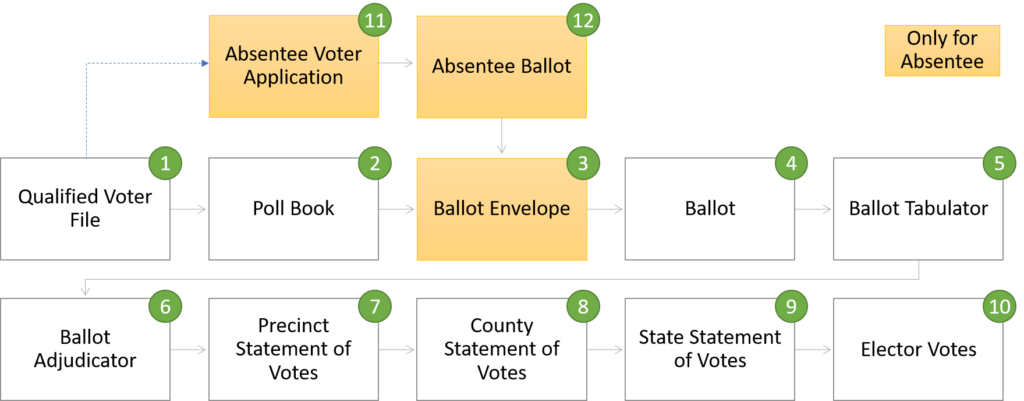
If the integrity of any one of these links is broken, the integrity of every link downstream of that breakage is compromised.
How is Chain of Custody maintained?
- Taking notes, including documentation of the recovery location, the time and date recovered or received, description of the item, condition of the item and any unusual markings on or alterations to the item.
- Marking and packaging the evidence.
- Sealing the evidence.
- Preparing the chain-of-custody record.
SOURCE: National Forensic Science Technology Center
Why is Chain of Custody important in an election?
The same reason Chain of Custody is important in criminal trials. The purpose of a Chain of Custody is to ensure that no one tampers with election artifacts in a manner that subverts the integrity of the election process. If any single link is broken in the chain of custody, the integrity of the entire election is broken resulting in no public confidence in the election results.
How is an Election Chain of Custody Broken?
The following table provides several ways in which individual links within the chain of custody for an election can be broken. It is not a comprehensive list, but it should provide important insights into how the chain of custody might be compromised if proper safeguards are not taken.
| ID | Link | How Broken |
| 1 | Qualified Voter File | Failure to remove deceased voters Failure to remove voters who have moved Failure to capture sufficient information to verify identity of voter Opening the database up to 3rd party data entry (e.g. Rock the Vote) Failure to track modifications to the Qualified Voter File Failure to save snapshot of database for election day |
| 2 | Poll Book (Precinct-specific extract of Qualified Voter File) | Enabling poll workers to add voters directly into poll book on election day Lax identity verification protocols regarding same day voter registration Failure to track modifications to the Poll Book Failure to seal poll book at end of election day operations |
| 3 | Ballot Envelope | No signature Lax signature verification protocols No match with poll book ballot number Failure to maintain a seal on ballot envelope container at end of election day operations |
| 4 | Ballot | Discarding ballots Adding new ballots without verifying identity of voters Failure to have representatives of both parties present when votes are transferred from a damaged or incompatible ballot format (e.g. military ballots) to one compatible with tabulation scanner Failure to maintain a seal on the ballot box at end of election day operations |
| 5 | Ballot Tabulator | Failure to perform robust public accuracy test Failure to demonstrate Zero report at start of election day tabulation Failure to print out precinct tapes at end of election day operations Failure to discard misfeeds and update poll book entries accordingly Tabulator connected to internet or local area network featuring workstations able to adjust vote tally Failure to secure the tabulator memory card containing images of scanned ballots at end of election day operations Failure to secure at end of election day operations |
| 6 | Ballot Adjudicator | Adjudicator connected to the internet or local area network featuring workstations able to adjust vote tally Failure to ensure adjudication is overseen by representatives of all parties Failure to secure at end of election day operations |
| 7 | Precinct Statement of Votes | Electronic transfer of data over the internet or Wi-Fi network Failure to secure data transfer media (e.g. flash drive) in a sealed package prior to transfer |
| 8 | County Statement of Votes | Failure to inspect seal containing precinct artifacts Failure to seal county package for transportation to state Data entry errors into county election results Electronic transfer of data over the internet or Wi-Fi network |
| 9 | State Statement of Votes | Failure to inspect seal containing county artifacts Data entry errors into state election results database |
| 10 | Electoral Votes | Brokered convention |
| 11 | Absentee Voter Application | Distribution of AV Applications to ineligible voters (~20% of Qualified Voter File ineligible) Collection of AV Applications by third parties willing to distribute to people willing to commit election fraud Failure to update poll book with absentee ballot number |
| 12 | Absentee Ballot | Ballot harvesting Ballots deposited in unsecured container (e.g. drop boxes) Ballots not secured within Clerk’s office Ballots not secured during transfer from voter to Clerk’s Office Ballots not secured during transfer from Clerk’s office to AV Counting Board |
If any single link is broken, the integrity of all election artifacts downstream of that artifact is broken including the all important election results.
In the State of Michigan, the chain of custody was clearly broken in multiple places as documented in over 200 signed affidavits. I observed first hand a complete disregard for Chain of Custody at the Detroit Absentee Voter Counting Board.
What Can We Do If Broken?
The following table provides a list of options which can be taken once a link in the chain of custody has been broken.
| Action | Pros | Cons |
| Ignore | No Effort | No public confidence in election results |
| Recount | Easy | Does not address any attempts to subvert election integrity upstream of “Ballot” artifact (Item 4) |
| Revote | Likely to ensure integrity of the election if broken links are repaired prior to revote | Labor intensive and likely to delay election results significantly |
| Audit | It should identify corrective actions necessary | May not be allowed to change the results of the election |
| Legislative Action | Mitigates need for expensive revote | Does not instill public confidence in results of election |
2020 Election Summary
The 2020 Election features thousands of affidavits asserting that links in election integrity were broken all across the battleground states of Michigan, Pennsylvania, Wisconsin, Arizona, Nevada, Georgia, and North Carolina.
Humpty Dumpty lies broken in the wake of the 2020 election. What remains to be seen is if Americans have the determination required to put Humpty Dumpty back together again…before the election results have been finalized.
REFERENCE:


Excellent information for now and future elections. Thank you so much Senator Colbeck.
What exactly did you observe
What can I do as a citizen of Texas to help fix this?
Thanks for this clear explanation of the process. A shame the national press does not provide this kind of clarity. But that’s why sites like Let’s Fix Stuff are springing up to fill the knowledge and integrity gap. Happy to support you and spread this important information.
#Imaprouddeplorable
#imaprouddeplorable
Great summary Patrick. It demonstrates the many points of potential failure/breakdown, and the actual flow when extrapolated with many more touch points for mail in voting really tells an important story. The more ballot touch points, the more opportunity for both accidental and nefarious errors/disenfranchisement. Ballot and vote count tampering can be spread across multiple touch points without sufficient controls…not too mention the impact of software impacts. Keep up the fine work, always let us know how we can help.
If party poll observers are ignored and signed sworn affidavits never see the light of day by a judge…what else can We The People or Politicians do?
Excellent info
Funny how the New York Times rejects that Mail-in ballots are ripe for fraud just like they rejected the Hunter Biden laptop story by dismissing it as Russian disinformation. Their credibility is shot and should remain so. Thanks for verifying what should be common sense for everyone ( even failed President Jimmy Carter knew this back in the late 70s).