By Patrick Colbeck
Mathematician and Cyber Engineer Draza Smith has been reviewing 2020 election night reporting data for quite some time. I recently heard a presentation of hers where she raised questions about the incremental vote tallies from the New York Times election night reporting data stream. She noted that a plot of these incremental vote tallies indicated the presence of what is referred to as a PID Controller in engineering circles.
As an engineer who has dabbled in control system analysis and design, I decided to investigate further.
What is a PID “Controller”?
Digital controllers are used to control the temperature in homes. Cruise controls in cars are used to control speed. Planes use autopilot controls to keep a plane in level flight or even reach a specific destination. Is it really that difficult to believe that there are people in this world of electronic voting systems who would seek to control the outcome of elections? If so, what would that look like?
The simplest type of controller design is simply an open loop controller that would change the vote tally based upon a predetermined formula. There would be no need to connect electronic voting machines to the internet in order to execute vote changes in this manner. Someone need only identify a formula by which votes would be shifted from one or more candidates to another. This formula could be embedded into software or hardware any time prior to tabulation of votes.
Of course, this fraud could be detected by a hand recount of ballots, but what if there was no incentive to perform a recount because the expected candidate still won the precincts they were expected to win? In a statewide election, there are red precincts and blue precincts. If one were to fraudulently “shave” 3-5% from the “easy win” precincts for a given candidate through an open loop controller, it is conceivable that the cumulative “shaved” votes would be sufficient to tip the scales of victory in favor of another candidate. As long as the perpetrator does not get greedy, there would likely be no push to perform a hand recount. If there was a push for a hand recount, any such recount would likely be preceded by legal actions such as injunctions that would cause delays until a “repositioning” of physical ballots could be orchestrated. Recounts of scanned ballot images as opposed to physical ballots would not be sufficient to detect this fraud. Ballot images are simply electronic files. If there was a fake ballot image repository embedded on a storage device or there was an internet connection allowing the import of ballot images to the ballot image storage device, ballot images can be inserted or deleted to ensure that the fraudulent vote tally would not be detected by a recount of ballot images.
The significant limitation of open loop controllers is that a successful outcome depends heavily upon an accurate prediction of voter turnout and how many votes would be needed to steal the election. This risk can be mitigated through the use of another type of control method referred to as a closed loop or feedback control system. A closed loop controller would be able to adjust the shifting of votes based upon variables such as voter turnout. Unlike open loop controllers, closed loop controllers that depend upon external data such as the statewide vote tally would need to receive that data somehow. This is one reason that any connection of voting equipment to the internet prior to certification of the election would be suspect.
A PID Controller is a unique classification of controllers typically used in closed loop systems to achieve a specific setpoint.
P = Proportional
I = Integral
D = Derivative
The following video by RealPars on YouTube provides an excellent overview of PID controllers and how their performance can be adjusted to achieve desired outcomes.
You may have noticed that tuning each of the parameters in a PID controller leads to changes in the output variable over time. The outputs of PID controllers have unique signatures akin to “fingerprints” that control system engineers can recognize.
The following video by the PID Explained Team provides an excellent description how “tuning” PID control parameters can be recognized in plots of the setpoint variable overtime.
A PID controller signature can be recognized as follows:
- As proportional gain is increased, the output variable value increases towards the desired setpoint. Too low of a gain may mean you never reach your setpoint. As proportional gain is increased, it induces oscillations from positive increments to negative increments towards the setpoint. Too much gain leads to instability in the output variable.
- Adjustments to the integral gain result in tradeoffs between steady state versus transient performance. Lower integral gain values result in better steady state performance (e.g. setpoint precision). Higher integral gain values ensure better response time (e.g. reach setpoint faster).
- Adjustments to derivative gain values are used to minimize any overshoot of the setpoint. Minimizing overshoot would minimize the risk of revealing negative proportional gain increments.
- Adjustments to the setpoint result in a “reset” of the output variable.
In an election, the setpoint variable would likely be the percentage of votes for a given candidate. Plots of election night vote tally increments over time could be examined for any evidence of a PID Controller signature.
What evidence of PID control can be seen in election night reporting?
Let’s review New York Times election night reports for the presidential race in Michigan. It shows evidence of a setpoint reset for a PID controller.
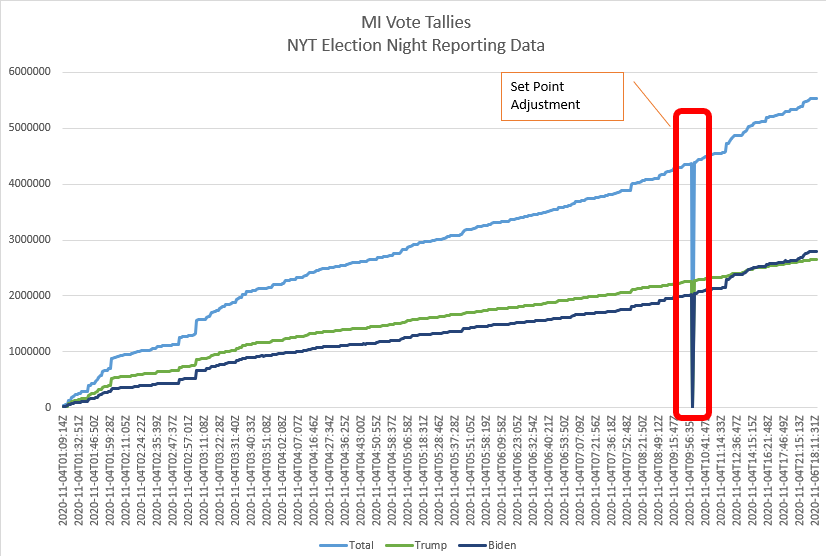
Let’s look at a plot of the relative vote percentage over time rather than cumulative votes. It shows clear evidence of proportional gain spikes.
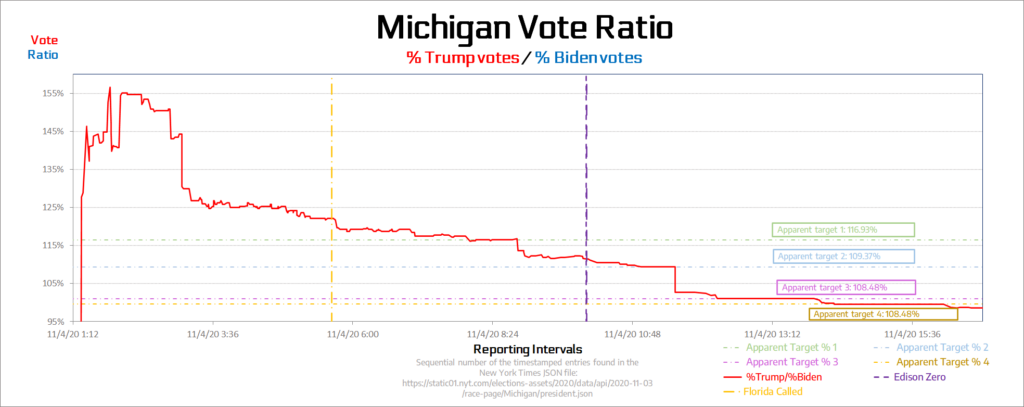
What about any evidence of negative vote increments?
Sure enough, there are multiple examples of negative vote increments indicative of vote tally oscillations.
First, let’s look at Wisconsin.
Now, let’s look at Pennsylvania.
Is there evidence of anyone applying control system analysis and design methods to elections?
Any sophisticated attempt to control election outcomes would likely be preceded by patents, design manuals or technical whitepapers tied to the design of digital controllers able to adjust election outcomes to achieve a desired election result with minimal risk of discovery.
Is there any evidence of someone attempting to control the election results in a manner that would benefit from these vulnerabilities?
As it turns out, yes. And it comes from a very interesting source in light of the events of 2020 and 2021.
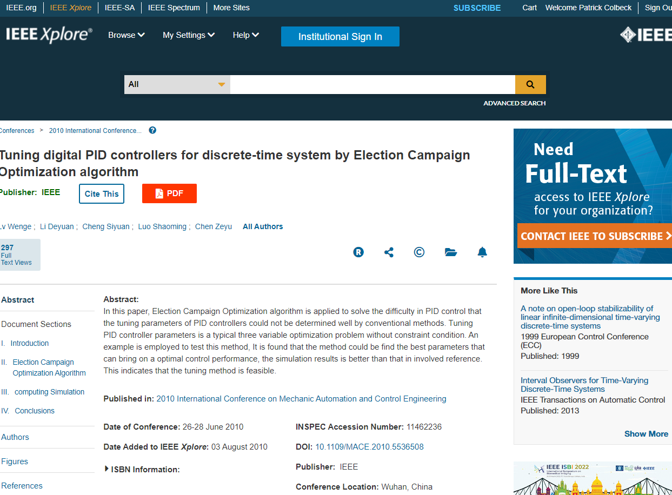
A whitepaper on the use of PID Controllers to “Optimize” Election Campaign results was presented by faculty at the Guangdong University of Technology at 2010 IEEE Conference in Wuhan, China. Their effort was supported by the Provincial Science Foundation of Guangdong.
The paper goes on to specify how to optimize the tuning of P, I, and D gains to achieve specific objectives. They call this process Election Campaign Optimization or ECO for short.
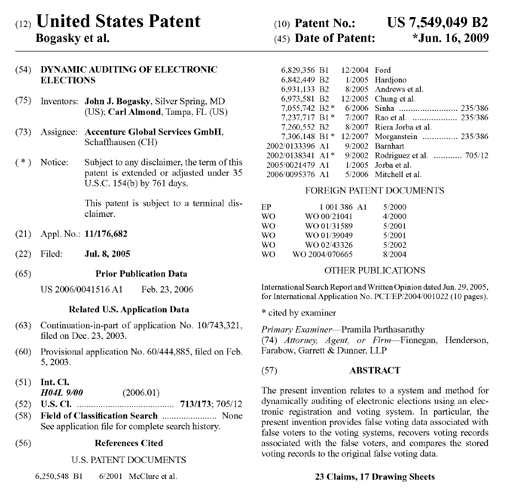
But wait…there’s more. As it turns out, there is additional evidence of technical solutions that appear to be geared to stealing elections. The following patent was discovered by Sidney Powell and her team.
In case you missed it, be sure to read the Abstract.

Interesting technical backdrop for the “most secure election in history”, don’t you think?
Conclusion
Electronic voting systems create significant risks to the integrity of elections by enabling digital manipulation of election records. Today’s electronic voting systems feature significant software and hardware vulnerabilities that are compounded by internet connections. Networked voting systems enable the implementation of sophisticated digital controllers. Digital controllers can be used in a stealthy manner to convert our “elections” into “selections”. This should never be tolerated.



Great article. Thanks for this explanation.
Awesome write up and right in line with with what I have been theorizing a bit. Similar to PID would be a fractional vote feature embedded in each voting application that can be used to invisibly, yet substantially, alter election outcomes by pre-setting desired vote percentages to redistribute votes. Instead of “1” the vote is allowed to be 1/2, or 1+7/8, or any other value that is not a whole number. Weighting a race removes the principle of “one person-one vote” to allow some votes to be counted as less than one or more than one. Places to look for this activity would be: The “Summary” vote tally, which provides overall election totals for each race on Election Night, The “Statement of Votes Cast”, which provides detailed results by precinct and voting method (ie. Polling, absentee, early, provisional) and The “undervote” count. Fractionalizing the “Statement of Votes Cast” allows an extraordinary amount of precision, enabling alteration of results by specific voting machine, absentee batch, or precinct. Vote results can be altered for certain polling places, neighborhoods, and can parse out precincts within a mixed batch of early or absentee votes. Fractionalizing the undervote category allows reallocation of valid votes into undervotes. So as votes accumulate, the number of votes in a race can somehow get subtracted as new votes were added. This can be achieved through machines with floating point capabilities and the command in the source code would be “DOUBLE”. So something like this:
One person, one vote: “1”
One person, 3/5 of a vote: “0.60”
One person, one-and-a-half votes: “1.5”
What it might look like in the SQL source code:
ALTER TABLE SumCandidateCounter
ALTER COLUMN TotalVotes DOUBLE
ALTER TABLE SumRaceCounter
ALTER COLUMN NumberOfUnderVotes DOUBLE
CREATE TABLE SumCandidateCounter (
ReportunitId INT,
VCenterId INT,
CounterGroupId INT,
CandVGroupId INT,
TotalVotes DOUBLE)
CREATE TABLE SumRaceCounter (
ReportunitId INT,
VCenterId INT,
CounterGroupId INT,
RaceId INT,
TimesCounted INT,
TimesBlankVoted INT,
TimesOverVoted INT,
NumberOfUnderVotes DOUBLE)
ALTER TABLE CandidateCounter
ALTER COLUMN TotalVotes DOUBLE
ALTER TABLE RaceCounter ”
ALTER COLUMN NumberOfUnderVotes DOUBLE
# Contains the candidate counts for the race
CREATE TABLE CandidateCounter (
CounterBatchId INT,
ReportunitId INT,
CounterGroupId INT,
CandVGroupId INT,
TotalVotes DOUBLE
Number of votes)
CREATE TABLE SumCandidateCounter (
ReportunitId INT,
VCenterId INT,
CounterGroupId INT,
CandVGroupId INT,
TotalVotes DOUBLE)
Another example:
Overvotes are counted as whole numbers but undervotes are counted as decimals. The existing votes can be transferred among candidates according to pre-set percentages. Because the decimalized vote feature allows an extraordinary amount of precision, it is possible to instruct the voting system to produce a landslide, a squeaker, or just a solid but uncontroversial win. The programmer definitely has clean up code written into the script With the software automatically rounding off decimalized votes in its results so you will never see them.
We definitely need to get access to all of the source code used in these voting machines. Using the but but but it’s “Proprietary” and is a corporate secret excuse needs to get blown out of the water and these machines need a beat down like the copier from Office Space.
Good